Filters
 10:00
10:00
Dangerous comments! What, where and how to post on YouTube?
Is it possible to write these or other things in the comments? And in general,...
4 days ago 21:18
21:18
How is Telegram connected to the FSB? What does this mean for you personally?
"People in Russia, Ukraine, the USA, India and many other countries trust it with their...
5 days ago 44:31
44:31
Pavel Belousov, Nadiyno.org: How to avoid falling for the bait of internet scammers?
Pavel Belousov, technical lead for the Nadiyno.org digital help hotline, gives recommendations to Internet users:...
1 week ago 14:28
14:28
Getting ready for the cybersecurity certification exam — Lab 1 (API) — Delete users without permissions
"Getting ready to obtain a cybersecurity certification together by solving lab exercises. The labs used...
1 week ago 31:40
31:40
Taiwanese investigative journalist Jason Liu visits Vitaly Moroz
eQtalk is the original content of the eQtv channel. In the frame, a representative of...
2 weeks ago 01:00
01:00
Why is it important for organizations to establish cooperation with CERT-UA in advance?
How to establish cooperation with CERT-UA for effective protection against cyberattacks. Team leader Evgeniya Nakonechnaya...
2 weeks ago 05:59
05:59
Jami messenger: messenger with Briar-like security and Telegram functionality
"There are many secure messengers, but they all sacrifice functionality for security. Jami differs from...
2 weeks ago 06:12
06:12
Guerrilla texting: encrypted text messages in case of an internet outage.
"The probability of Internet shutdown in Russia is high, but we can say with a...
3 weeks ago 11:54
11:54
How the U.S. Ambassador Was Spied on for 7 Years with an Invisible Bug—and Its Surprising Link to Electronic Music
In 1945, Soviet spies scored a major victory over their American colleagues: they managed to...
3 weeks ago 01:17:35
01:17:35
Anonymization and creating a virtual identity
Analysis of methods of ensuring anonymity on the Internet: how to lead an active digital...
3 weeks ago 01:02:26
01:02:26
Oleksandr Glushchenko, Pavlo Belousov: MAХ messenger – delete it IMMEDIATELY!
Pavel Belousov, technical lead for the Nadiyno.org digital help hotline, gives recommendations to Internet users:...
3 weeks ago 03:19
03:19
Six Easy Steps to Get Us Addicted To Our Phones
How and why we become addicted to our Phones
3 weeks ago 01:54:53
01:54:53
Pavlo Belousov, Nadiyno.org: How to improve the security of your cyber perimeter?
Pavel Belousov, technical lead for the Nadiyno.org digital help hotline, gives recommendations to Internet users:...
3 weeks ago 17:37
17:37
You need anonymity online. And that's why
Anonymity on the Internet is not only a tool of hackers, but also a key...
4 weeks ago 08:04
08:04
Bypassing blocking - banned content. Can we get out of this?
From March 1, 2024, Roskomnadzor will begin to block instructions for bypassing the blocks. In...
1 month ago 01:32
01:32
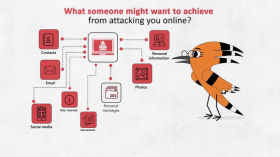
Have I been hacked
Digital security course: How to hack someone's account, how to understand whether it's reliably protected...
1 month ago 02:14
02:14
How to Create and Keep Strong Passwords
Digital security course: How to create and store strong passwords
1 month ago 10:08
10:08
Cybersecurity cert prep: Lab 5 (SSRF) — building a custom intruder to scan an internal network
"Getting ready to obtain a cybersecurity certification together by solving lab exercises. The labs used...
1 month ago